Cyber criminals are using ever sneakier tactics to avoid detection of their botnets and C&C servers. One such tactic botnet masters are using is fast-flux DNS. Fast-flux DNS was originally implemented by the Storm Worm botnet masters in 2007. Since then, numerous malware variants have used fast-flux DNS to avoid detection by the authorities.
Fast-flux DNS involves associating many IP addresses with a single fully qualified domain name (FQDN). Botnet masters rotate the IP addresses in this pool at high frequencies, sometimes as often as once every 5 minutes. Thereby creating an ever changing network of compromised hosts known as fast-flux agents. Cybercriminals use this DNS technique to obscure the true origin of malicious sites and other resources. This allows C&C infrastructure to stay online for longer periods of time.
In a fast-flux network the command and control infrastructure is often referred to as the mothership. The mothership consists of numerous backend servers that each facilitate the operation of the botnet.
When a compromised host attempts to communicate with the mothership, it first makes a request to a fast-flux agent. The fast-flux agent then transparently proxies the request to the mothership.
What is a fast-flux network?
We know that fast-flux works by rapidly changing IP addresses assigned to a domain name. Now let us take a deeper look at how this is accomplished.
There are two types of fast flux networks:
- Single-flux
- Double-flux
Single-flux networks
Single flux DNS works by rapidly assigning multiple A or AAAA records to a domain name and constantly rotating the active IP addresses. These IP addresses belong to compromised hosts which are known as fast-flux agents.
Each fast-flux agent acts as a reverse proxy to the command and control infrastructure. When a compromised host resolves the domain name of its C2 infrastructure, the name server sends the IP of a fast-flux agent. This keeps the mothership hidden behind a vast network of ever changing proxy servers. As such, a compromised host only ever communicates directly with a fast-flux agent, never with the C&C servers.
In single-flux networks the authoritative name server is often hosted on bullet-proof hosting to further increase resistance against takedown. Operators of bullet proof hosting services typically reside in areas with little to no established cybersecurity laws and generally do not comply with takedown requests.
This makes it very difficult for security researchers to identify and take down the C&C servers. Even if a fast-flux agent is identified and taken offline, another node is always ready to take its place.
Double-flux networks
With single-flux only the domain’s A records are changing. Double-flux networks add an additional layer of misdirection by also changing the authoritative name server records. Network masters rotate not only the A records, as with single flux, but also the NS addresses. When an infected client attempts to resolve the domain name, it first gets the IP address of the authoritative name server. This is just another fast-flux agent which forwards the DNS request on the to the C&C servers which handle the DNS resolution.
Fast-flux provides an intricate web of misdirection making detection difficult, and take-down almost impossible.
With an ever changing network of endpoints and name servers there is no single point of failure in the network. Shutdown a node serving requests for a malicious website, another pops up to take its place. Shutdown the name server serving DNS requests for a malicious domain, another name server steps in and starts serving requests.
What are fast-flux networks used for?
As you can see, fast-flux networks are quite powerful in their resilience. Botnet masters may have thousands of fast-flux agents at their disposal allowing them to create massive proxy networks.
This resilience and protection makes fast-flux networks the tool of choice for attackers looking to serve any less than legit content. Cybercriminals use fast-flux networks for serving malicious downloads, phishing sites, illegal marketplace sites, and even worse things such as sites dealing in child pornography and sex trafficking.
The sensitive or malicious material is stored on the mothership. The fast-flux network acts as a layer of reverse proxies disguising the true origin of the malicious files. This is what makes the fast-flux network so powerful. Authorities are only ever able to shutdown a fast-flux node, not the actual backend content. As soon as another node takes its place, the content is available again.
How do fast-flux networks work?
Network masters typically divide their fast flux networks into 2 or more sub-networks. The main hosting sub-network is used for directing traffic to phishing sites, or other malicious content. While the secondary C2 sub-network is used for managing and monitoring the botnet.
Single-flux example
Let’s take a look at a simple example of how a compromised host may contact its command and control infrastructure. In this example let’s assume that the domain name of the command and control channel of the mothership is c2.mother.ship.
First the compromised host makes a DNS request (1) to look up the address associated with the command and control domain, c2.mother.ship.
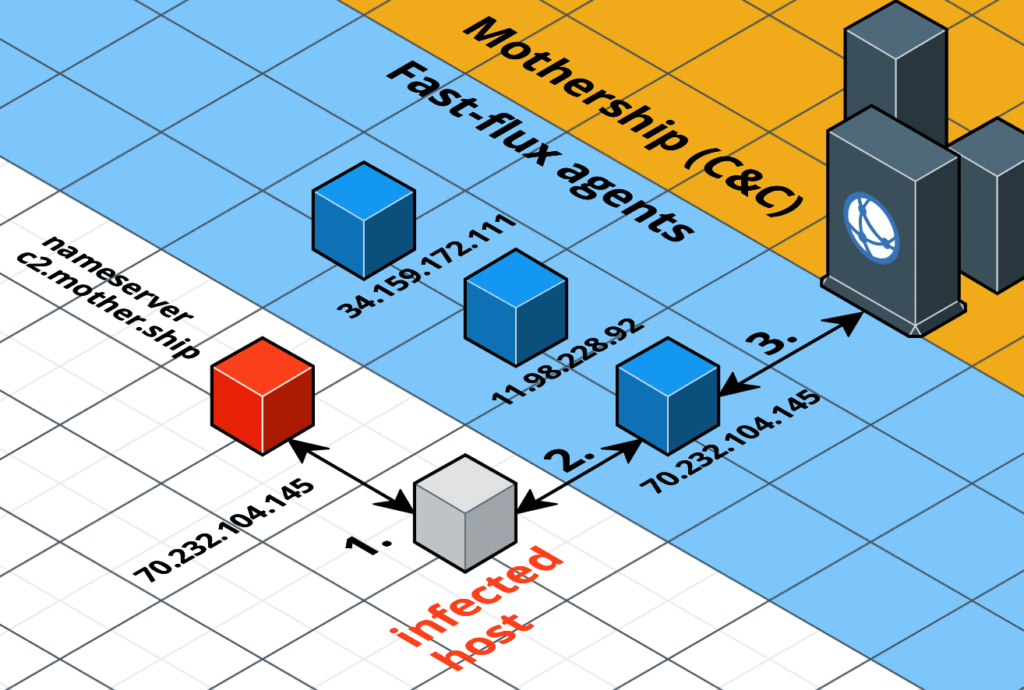
The name server returns the IP address of a fast-flux agent. The compromised host then makes a request to the fast-flux agent (2). When the fast-flux agent receives the request it transparently forwards the request on to the C2 server (3). The C2 server returns the appropriate content to the fast-flux agent. Finally, the fast-flux agent returns this content to the compromised host. The compromised host does not even know the C2 server actually exists. It only ever communicates with one of the thousands of fast-flux agents.
Of course this is a simplified example. In a real world fast-flux network requests are often routed between multiple different fast-flux agents before finally reaching the command and control server.
Double-flux example
Now that we have seen single-flux in action, let us take a look at how double-flux works with another example. Once again our infected host tries to contact c2.mother.ship. In order to locate the authoritative name server, the infected host first queries the .ship TLD for the authoritative name server for the c2.mother.ship domain (1).
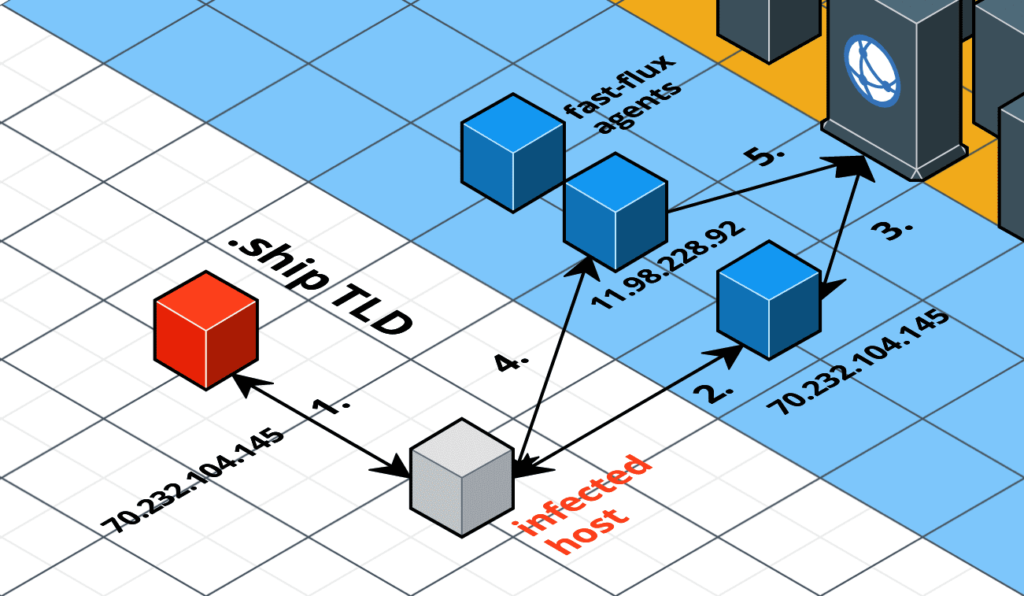
The .ship TLD server responds with the address of a fast-flux agent as the authoritative NS. Now the infected host sends a DNS query (or more accurately, the infected host’s DNS resolver) to the fast-flux agent (2). This fast-flux agent forwards the DNS request on to the mothership for resolution (3). The mother ship sends back the IP address of a fast-flux agent active on this domain. Once the infected host receives the IP address of the fast-flux agent, it makes a request to that agent (4). That agent once again forwards the request to the mothership and responds with the content served by the mothership (5).
Detecting fast-flux networks
The very nature of fast-flux networks makes them difficult to investigate. It may take years for teams to finally track down the mothership and dismantle the botnet. Fast-flux networks typically span many countries meaning varying levels of regulations apply. Dealing with cross-border bureaucratic red tape slows many investigations to a crawl. This is why some botnets such as Avalanche remained operational for years before they were finally shutdown.
Interested in how a host gets compromised in the first place? Check out my article on the cyber kill chain, the sequence of events from reconnaissance to compromise and beyond.
We hope you’ve enjoyed taking an in-depth look at the fast-flux DNS technique. Leave us your thoughts in a comment below!
Great content! Super high-quality! Keep it up! 🙂
Really enjoy reading, great work explaining!
Thanks very much.
What about dns propagation time?
PS: I’d change “As such, a compromised host” for a infected host, for clarification 🙂
PS2: In mitigation passive DNS services might be a good option. ex farsightsecurity