Greetings my fellow hackers! This will be a multi-part DVWA hacking tutorial covering many practical examples for exploiting vulnerabilities, gaining a foothold, and taking over the host.
So you’ve got DVWA up and running, you see some kind of a login page, and have no idea where to get started? Fear not! I’ve been where you are. In this multi-part DVWA hacking tutorial I will cover numerous techniques for a full takeover of DVWA. Throughout this tutorial you’ll learn many hacking techniques and if you follow along you will learn how to practice hacking as well.
Using This Tutorial
To follow along with this tutorial you will need an instance of DVWA up and running. If you still need to install DVWA check out our tutorial: How to install DVWA in Ubuntu
Before we get started, we need to talk about DVWA security levels. Since DVWA is a tool for learning about cybersecurity, the authors implemented “levels” of difficulty. A higher security level generally means you’ll have a harder time exploiting vulnerabilities. For these tutorials, unless otherwise noted, we will be using the LOW security level.
Once you get more comfortable finding and exploiting vulnerabilities, try again on a higher security level. You will most likely find you need to change tactics!
DVWA Security Levels
There are 4 security levels in DVWA. These range from LOW to IMPOSSIBLE and set the difficulty for attacking the application. The security levels also reveal how specific issues can be coded more securely.
LOW – This security level is completely vulnerable and has no security measures at all. It is meant to be an example of how web application vulnerabilities manifest through bad coding practices.
MED – This level is more difficult than low and illustrates bad security practices, where the developer has tried but failed to secure an application. This level will require more sophisticated exploitation techniques.
HIGH – This option is an extension to the medium difficulty, with a mixture of harder or alternative bad practices to attempt to secure the code. The vulnerability may not allow the same extent of exploitation.
IMPOSSIBLE – This level should be secure against all vulnerabilities. It is used to compare the vulnerable source code to the secure source code.
Login with the default user (admin/password) and select DVWA Security from the menu on the left. Select the desired security level, and click Save. A message will indicate the security level was changed.
After checking that the security level is set appropriately, we can begin. Lets get started with a classic and still effective attack: sql injection.
DVWA Hacking Tutorial: SQL Injection
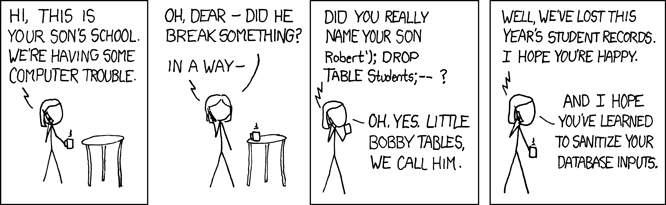
A SQL injection vulnerability occurs when user input is not properly sanitized before being used to form a database query. This timeless comic describes the issue nicely!
There are more than a handful SQL injection vulnerabilities in DVWA. We will start with the more obvious one by selecting SQL Injection from the left hand menu.
Exploration
We are presented with a form field asking for a User ID. This page looks like some kind of utility for looking up user information. Let us enter a random user id and see what happens. Why don’t we start with 1?
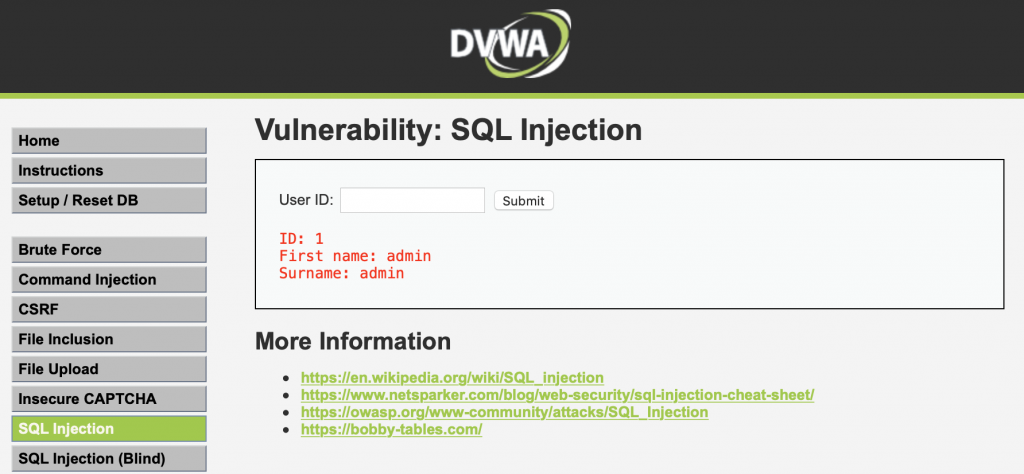
It looks like User ID 1 belongs to the admin user. This is good information to save for later, but for now we want to hack something! Based on the provided output we could speculate that the backend query might look something like this:
SELECT firstName, surname FROM users WHERE id='$id';Of course we are just speculating on the names of the columns. We are more interested in the actual structure of the query.
Exploitation
Let’s see what happens when we enter the following in the user ID field instead. Note: Be sure to copy the trailing space after the comment indicator: —
' or 1=1; -- The results should look a little different this time!
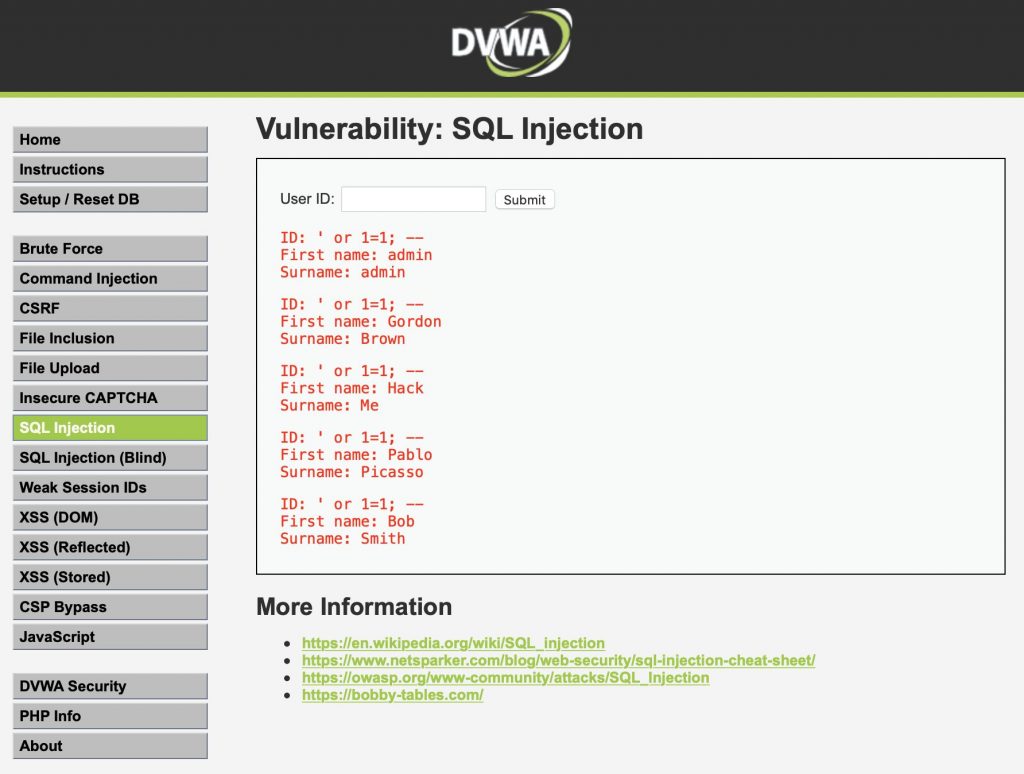
What just happened? The query now directly includes the user input. This makes the query end up actually looking like this:
SELECT firstName, surname FROM users WHERE id='' or 1=1; -- ';Now the WHERE clause is looking for any rows that match the condition id=” (never true) OR 1=1 (always true). This causes the query to return all users on the application. By adding a comment to the end of our input we instruct the query processor to ignore the rest of the line so we don’t get an error because of the additional apostrophe.
We now have a complete user listing of all users. With this information, we could now launch additional attacks. For instance, we could iteratively test User ID values and match them to individual users.
With a little imagination, and a SQL injection vulnerability, there is no limit to the damage an attacker can do to a vulnerable system.
DVWA Hacking Tutorial: XSS
Cross Site Scripting (XSS) is a type of vulnerability that allows for the execution of Javascript (or other) code for cookie stealing, information scraping, and in extreme cases, hackers can use XSS to download malware without any action by the user.
Let us select the XSS (Reflected) module from the menu on the left. Then we will once again begin with a benign entry to figure out what the application is doing.
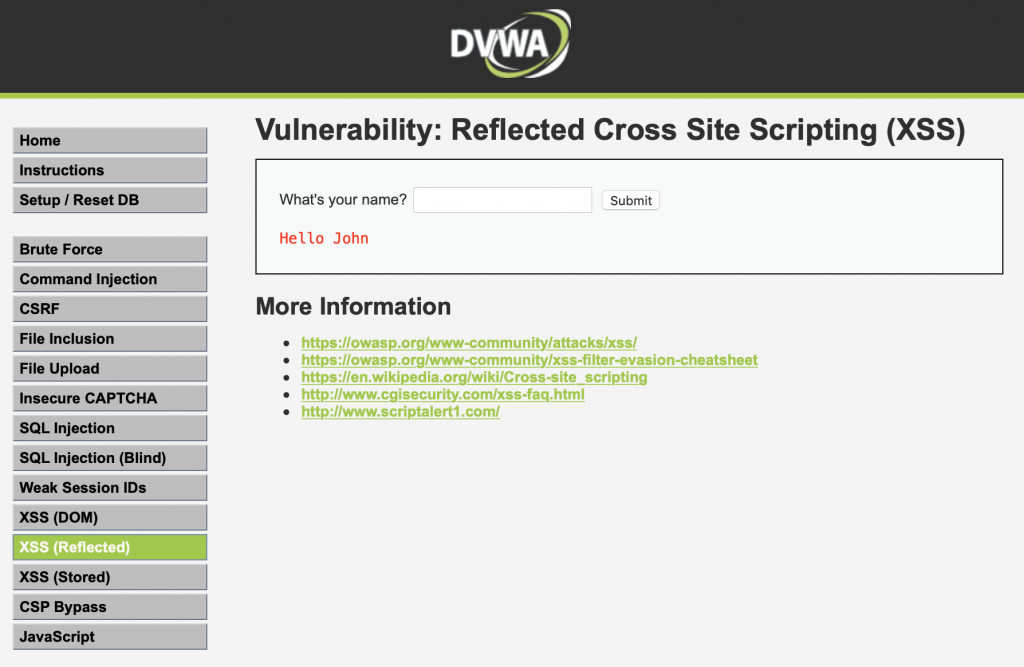
It looks as though the application is displaying our input directly on the page! This is often the first clue to a XSS vulnerability. Now we can test if the application does any filtering on the input.
This time let us include a little Javascript this time and display an alert window with our cookie if we are successful.
<script>alert(document.cookie);</script>Once again the application includes our input directly on the page. As a result, we should see an alert window pop-up with our PHPSESSID and security level cookies.
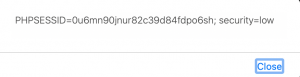
Next time it might not be so easy. Even poorly implemented XSS filters will often remove < and > or look specifically for <script> tags. Evasion of XSS filters is an art in itself. Check out the XSS filter evasion cheat sheet and try again on a higher security level.
Wrapping Up
Hopefully this introductory DVWA hacking tutorial has taught you a few basic techniques to use when starting a penetration testing exercise. Check back soon for part 2 of this DVWA hacking tutorial for more advanced techniques and attacks. Did this tutorial help you? Was it horrible? Let us know in the comments below!