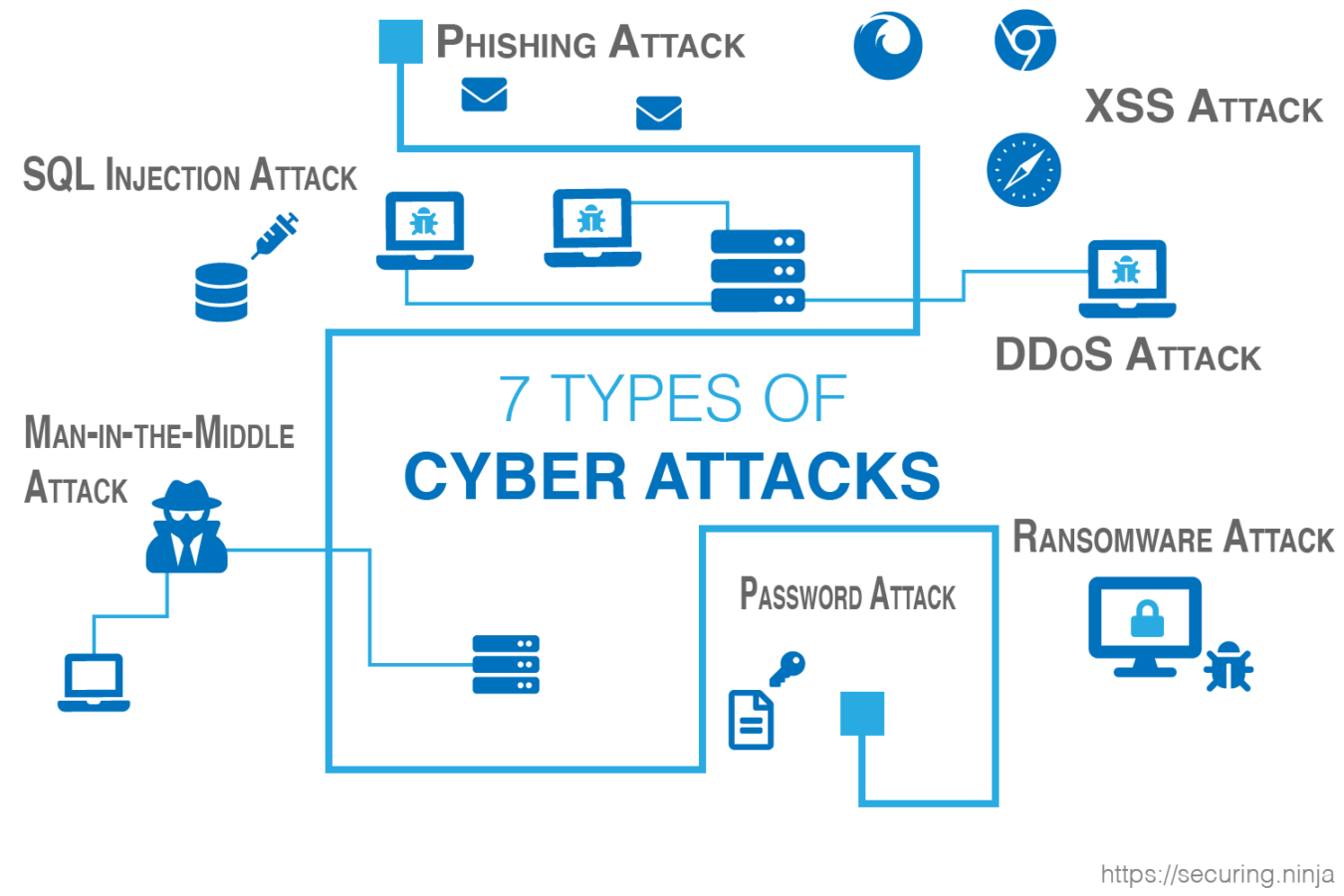
7 Types of Cyber Attacks That Could Be Targeting You Right Now!
Share this… Facebook Pinterest Twitter Linkedin RedditWelcome back to another informative article by SecuringNinja. Today we will explain the 7 most common types of cyber attacks that cyber criminals use everyday. Fear not, we will also share tips and tricks to protect against these types of cyber attacks. Cyber criminals are continuously evolving their tactics […]