Welcome back fellow hackers! Today we will show you how to install DVWA in Ubuntu. What is this DVWA? Why do I need it? Fear not, we will answer all your questions in time.
We often get the question from our readers: “what is the best way to practice hacking?” One of the best ways is through practice. That is where the Damn Vulnerable Web Application comes in. This is a nifty little web application that is, as the name implies, damn vulnerable. The application can be a little tricky for newcomers to install so we will show you how to install DVWA in Ubuntu. If you’re wondering how to install DVWA in Kali Linux you can follow these instructions as well. They should be similar enough for use on Kali. If you run into any issues feel free to leave us a comment below!
What is DVWA?
The Damn Vulnerable Web Application (DVWA) is a vulnerable web application designed for aspiring and experienced hackers alike to practice their skills and techniques. It is also a great tool for teaching about secure development practices.
Today we will show you how to install DVWA in Ubuntu so you can get started practicing your hacking skills.
Remember: Never expose your DVWA instance to the Internet! It is DAMN VULNERABLE and will be compromised!
How to Install DVWA in Ubuntu
Lets get right into it.
This tutorial assumes you have a fresh Ubuntu 20.04 LTS instance ready to go. If you don’t have an Ubuntu VM set up yet, check out our tutorial: How to build a virtual penetration testing lab
Make sure you have access to a user with sudo and lets get started!
First we will update the server. Then we will install the required packages:
sudo apt update && sudo apt upgrade -y
sudo apt -y install apache2 mariadb-server php php-mysqli php-gd libapache2-mod-php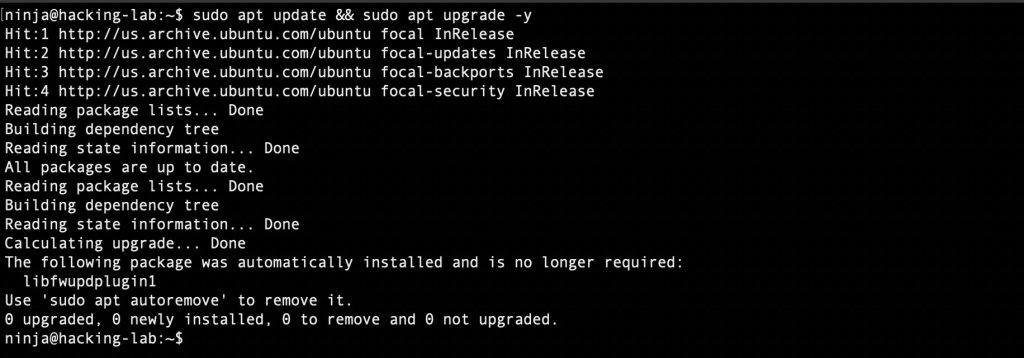
Prepare the database
Now we need to perform the initial database set up.
sudo mysql_secure_installationAnswer yes to the prompts and be sure to set a root password.
Now we can create a database and user.
CREATE DATABASE dvwa;
CREATE USER 'dvwa'@'localhost' IDENTIFIED BY 'password';
GRANT ALL PRIVILEGES ON dvwa.* TO 'dvwa'@'localhost' IDENTIFIED BY 'password';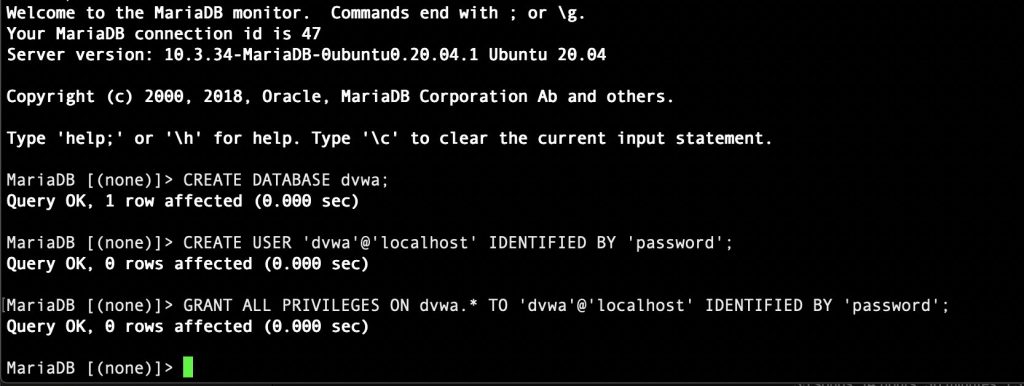
Install the Application
After creating the database, we can download the DVWA source code. This is as simple as changing into the target directory and cloning the code from Github.
cd /var/www/html
sudo git clone https://github.com/digininja/DVWA.git .
sudo chown -R www-data:www-data /var/www/html/*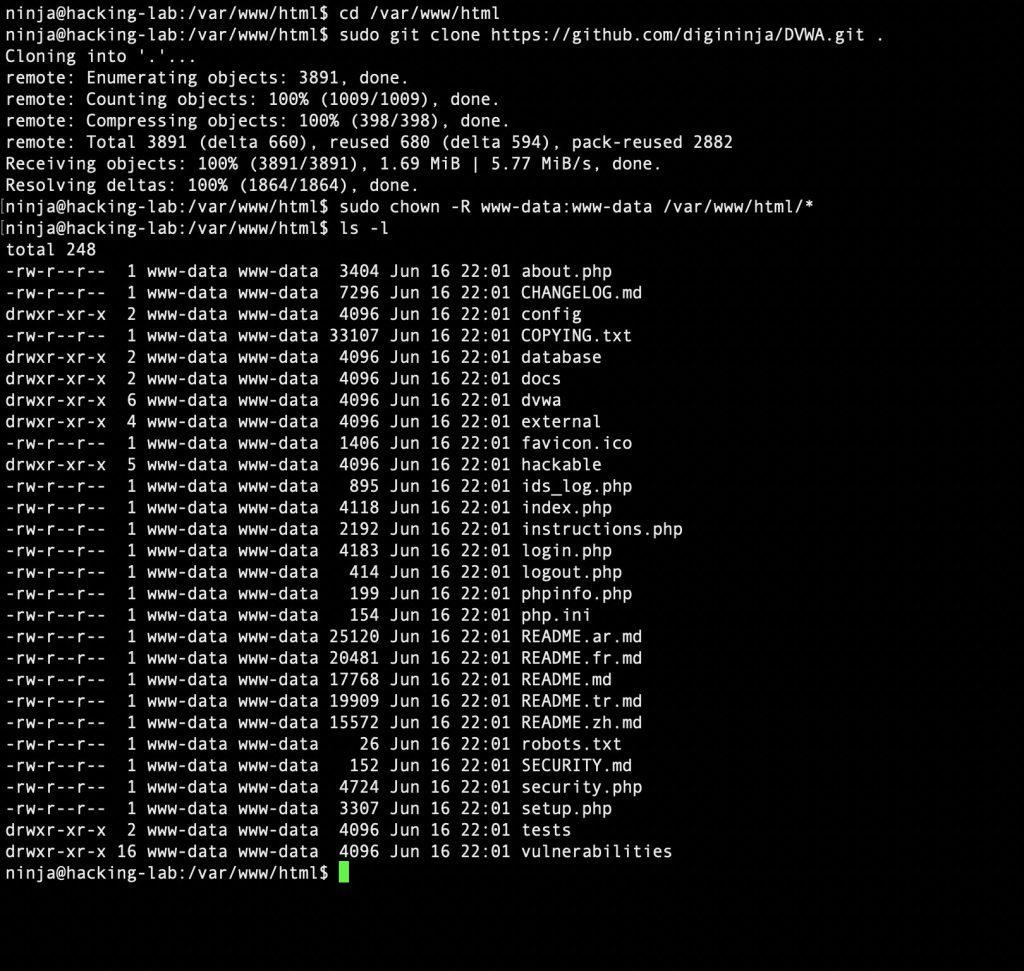
Next we will need to configure the application. This is as simple as copying the example configuration file, and changing the database connection parameters.
cp /var/www/html/config/config.inc.php.dist /var/www/html/config/config.inc.phpNow simply open the configuration file in your favorite text editor and update the database connection parameters with the username and password you created earlier.
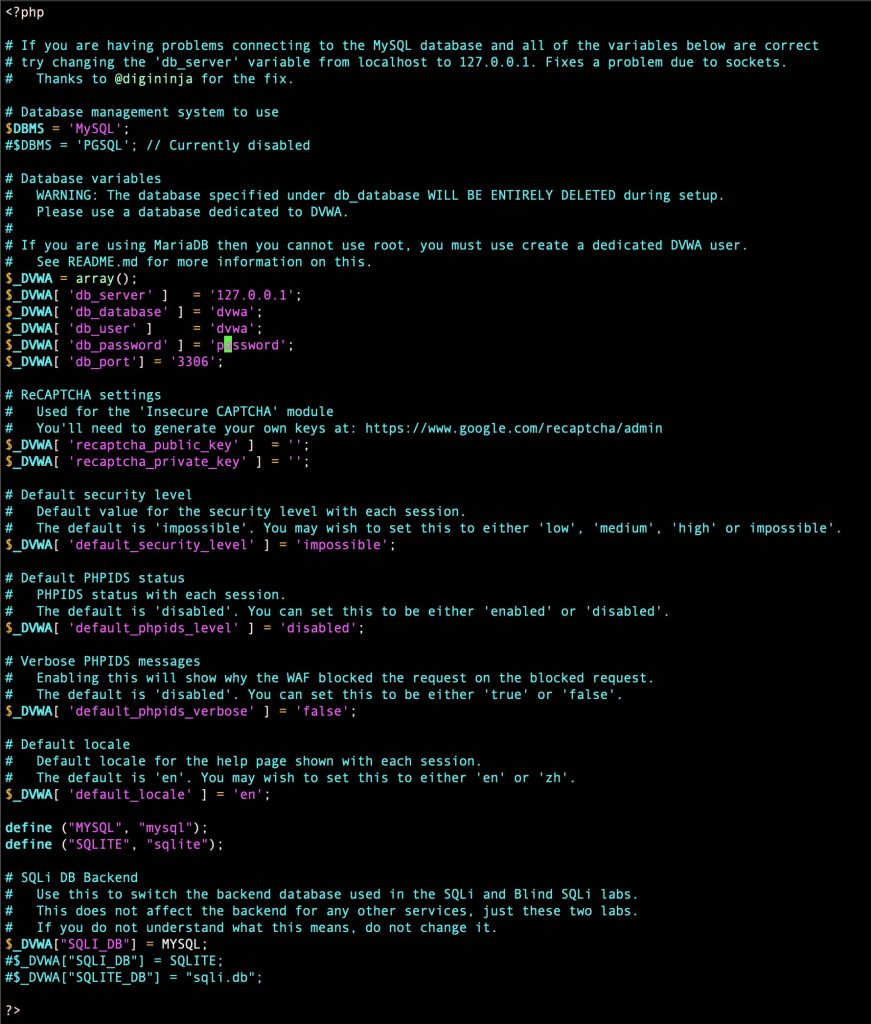
After configuration, the application should be accessible in a web browser. Your IP may vary depending on how you access your VM or server.
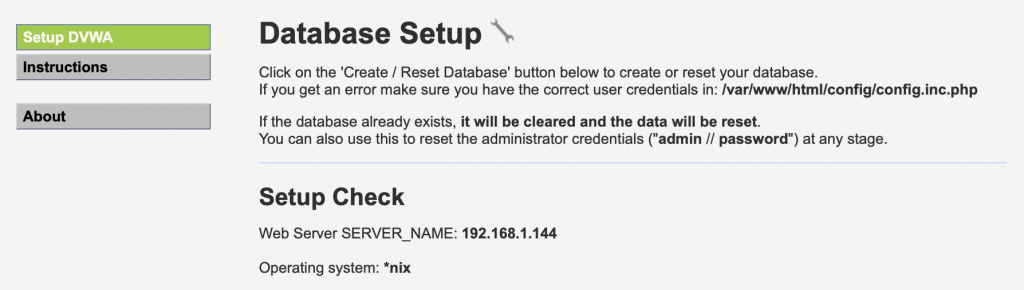
http://192.168.1.120/The last step is to run the database creation. This is as simple as clicking “Setup DVWA” in the upper left, and then clicking “Create / Reset Database”. After creating the database, the application is ready to go. Time to get to work!
Final Thoughts
Now that we’ve shown how to install DVWA in Ubuntu you should have a juicy target for practicing a variety of hacking techniques. You may want to browse the site using your regular web-browser and see if you notice any potential avenues of attack. Not sure where to start? You can use the default credentials of admin and password to access the application. Happy hacking!

One thought on “How to Install DVWA in Ubuntu”
-
Pingback: DVWA Hacking Tutorial - Securing Ninja
Leave a Reply